April 08, 2020 By BlueAlly

By Lior Cohen | April 08, 2020
In my previous blog, I highlighted security considerations for supporting the rapid rollout of large scale, high-speed VPN connectivity to increase secure remote worker capacity. Once this occurs, most organizations are looking to maintain business continuity through a remote worker strategy. Their employees are logging into the corporate network from their home offices using a combination of corporate-provided and personal devices. However, the results can be mixed.
Many corporate resources, especially at the core network, were not designed for this sudden load of connections and traffic. Many organizations are struggling to provide consistent access to critical applications and data. Others are building complicated ad hoc environments to support challenges as they arise, which has extremely stretched IT resources. And along this process, security may have taken a back seat to simply providing connectivity.
Three Key Challenges
Because this transition to a remote worker environment has expanded the potential attack surface, we have seen a resulting spike in criminal activity targeting this new paradigm. In this blog, I will outline the second phase of an organization’s remote work strategy – one that goes beyond providing a VPN tunnel back to the network.
Leveraging the cloud to augment on-premises capacity and to enable new functionalities provides scalable, manageable and secure remote access with minimal IT overhead and no need to deploy additional devices. Using the Fortinet Security Fabric products and functionalities deployed in the cloud quickly provides increased remote access capacity and application security capabilities to address the following challenges many organizations are now facing.
The Remote Worker Challenge
First, critical applications and data deployed on-premises – many of which may have only been previously accessible by individuals inside the network – now need to be accessed remotely. Making these resources suddenly available to remote users introduces unexpected risks that may be challenging for organizations to address.
Second, more users than ever need remote access to applications and data. As a result, for many organizations, their remote connectivity capacity is being overwhelmed. And because addressing these requirements needs to be done rapidly, the provisioning of hardware is not feasible. As a result, access to business and productivity applications may be adversely impacted.
Application Access and Security
In order to maintain business continuity, organizations are stressed to open access to various business applications that support supply chain and service delivery business functionalities. In cases where dedicated site VPN connections were used to build secure transaction connectivity with partners or customers, there is now a need to enable internet access. In cases where in-person transactions were required, the need to open up applications to more third-party services and communications is also growing. The ability to open applications to more parties also increases the attack surface and in turn risk. This is why the need to secure these applications must be accounted for.
Productivity Tools
As users interact less in person, the use of SaaS productivity tools and email is especially critical for organizations to continue operating. Tools for collaboration, productivity and email are employees’ primary forms of communication, resulting in more information being shared over collaboration tools and email. Because of this, it is crucial that organizations are properly securing content and maintaining visibility into SaaS collaboration platforms.
Leveraging a Dynamic Nature of the Cloud
Since the Fortinet Security Fabric works consistently across physical, virtual and cloud-based environments, Fortinet customers have the opportunity to leverage its functionalities to address their urgent needs. Fortinet Security Fabric’s products and solutions are available for all major cloud provider platforms. Therefore, it extends organizations’ security infrastructure with a cloud-based solution, helping organizations address the emerging needs for connectivity and application security without adding operational complexity or requiring any capital expenditure – whether this is temporarily or a long-term approach.
Leveraging the cloud enables organizations to rapidly address new security and connectivity requirements. Spinning up on-demand instances of existing products enables our customers to augment the capacity they already have on-premises or in the cloud. This helps keep network and security teams operating in the same model while using a familiar and scalable solution to address growing interaction with customers, partners, vendors and end users. Provisioning can be immediate and can be retired once the need for enhanced capacity or capability no longer exists.
Addressing Six Critical Business Continuity Use Cases with Cloud Security
To help organizations with this transition, Fortinet outlines the main use cases organizations are facing in the following diagram:
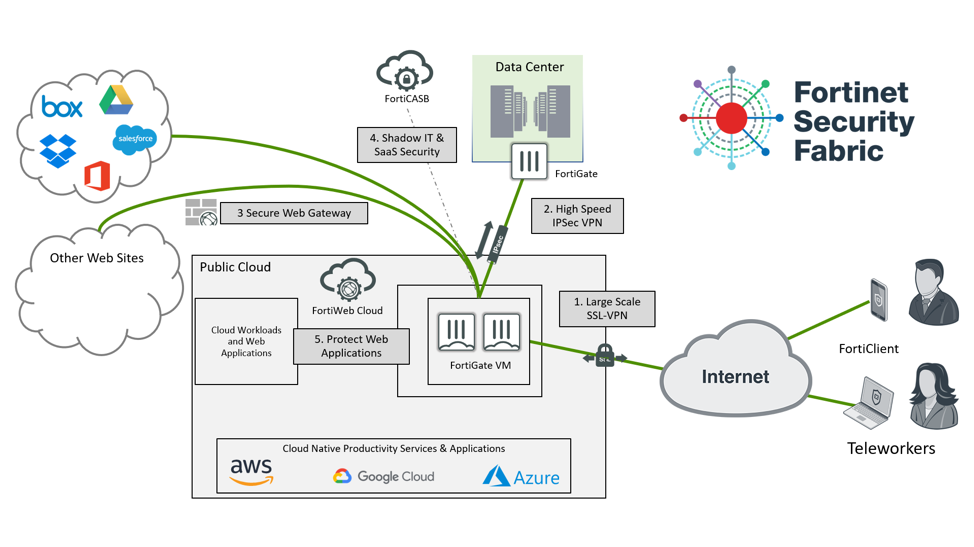
1. Scaling Remote Access VPN
There’s been a significant uptick in SSL VPN being used for large scale remote access VPN solutions. Leveraging tunneling capabilities available in SSL VPN can help organizations seamlessly extend security out to a large remote workforce connectivity solution while also using common network security practices that are likely in place in organizations with large user offices. Since each SSL user session is relatively small in terms of network traffic, high availability is easy to achieve by spreading VPN users across multiple VPN Gateways. FortiGate customers can safely implement auto-scaling and other manual scale out solutions to increase the overall SSL VPN capacity and availability without redesigning their existing deployment to implement significant scalability.
2. Scaling backend VPN tunnels to address impact of traffic increase
VPN tunnels connecting data centers and clouds may be more overloaded due to backend traffic supporting the larger volume of remote users, especially when it is compounded by increased application usage. Often cloud infrastructure limitations pertaining to specific compute and network resources available to customers limit the ability to meet traffic requirements. By leveraging advanced network acceleration and cloud resource aggregation capabilities, organizations can keep operational disruption to a minimum while addressing the increased demand. As an example, organizations can leverage larger virtual machine instances with more core and aggregate virtual network interfaces with FortiGate-VM in order to deliver very high bandwidth VPN tunnels. By leveraging these capabilities, organizations do not need to manage more firewalls or VPN tunnels – which would increase complexity – in order to support the growing scale of applications and user traffic. Additionally, SD-WAN policies can be implemented to reserve capacity for certain applications to ensure secure and available access. Ultimately providing the tools to scale security without impacting users or operations.
3. Mitigating Web Browsing Risks with Secure Web Gateway Capabilities
Fortinet’s Secure Web Gateway (SWG) solution, available for all FortiGate customers through their existing product, enables organizations to use application control for deep visibility into end user traffic, as well as to implement acceptable user policies for company owned devices. Its SSL inspection capabilities also enable it to provide insight into encrypted traffic to ensure that VPN connections don’t become transportation vehicles for malware or data theft.
4. Maintaining Visibility and Control Over SaaS Usage and Shadow IT
As the use of collaboration tools – such as Office 365, Box and Google Drive – from managed and unmanaged devices become more critical to ongoing business operations, the ability to maintain visibility of the content and usage of these tools remains a critical extension to remote user network security and connectivity. FortiCASB provides critical visibility and control for SaaS applications or the use of unsanctioned SaaS applications as Shadow IT. Leveraging FortiGate-VM for SWG functionalities in conjunction with FortiCASB helps maintain visibility across sanctioned and unsanctioned applications. IT teams can fine tune and optimize SaaS application security alerts and settings in FortiCASB to monitor SaaS usage, prevent data loss, and gain visibility into Shadow IT resources.
5. Securing Web Applications
As the need to open access to more applications becomes timelier and urgent, the challenge to rapidly provision the adequate protections and acquire expertise in securing these applications increases. To address this challenge, Fortinet provides an easy to use, dynamically available Web Application Security as a Service solution that can support the security of local and global web applications and mobile applications’ APIs. FortiWeb Cloud can offer organizations immediate value with a very easy-to-use and intuitive user interface, a long free trial period and no commitment for long term use.
For FortiWeb customers, it is very easy to expand FortiWeb on-premise deployments to the cloud with FortiWeb VM and leverage the consistent security management capabilities of FortiWeb Manager. It also enables customers to expand SAML and SSO capabilities from on-premise web applications to more applications protected by FortiWeb VM.
Reliable and Scalable Security for Remote Work
Organizations that have had or are in the midst of a transition to an enhanced remote work model can leverage the cloud to rapidly address immediate security requirements, and do so cost-effectively. By leveraging some of the capabilities outlined in this blog, organizations can quickly leverage the cloud to meet the demands of their recently expanded remote work while addressing business risks.
Enhancing the user experience and maintaining productivity enables workers to return to business as usual with limited disruptions. And for those organizations who consider making this model part of their “new normal,” web-based services enable them to scale long term while reducing both capital and operational overhead.
