An Analysis of Attacker Activity through NDR, EDR, and NGFW Data
These multi-dimensional analytical and response capabilities help teams detect any evidence of malicious behavior early in the attack life cycle, ultimately accelerating analysis and enabling analysts to respond to issues quickly.

Intrusions are complex to detect, as attackers continuously evolve their techniques to avoid exposure, progressing through multiple attack stages to remain undetected for an extended dwell time. Once they have successfully breached an organization, threat actors often use common practices, such as multi-hop proxies, combining malicious activity with legitimate network traffic, ingress tool transfers, and forced authentication to advance their efforts. These clever activities make it challenging for security teams to discover and distinguish between genuine and malicious activity.
To combat this challenge, security teams often use telemetry and observations from multiple security tools to gain a complete picture of the events happening within their networks. Security teams need unified visibility across the environment, correlating and analyzing multiple data sources to gain more context and help them decide on the right response and mitigation strategies.
This white paper takes a closer look at the valuable insights security teams can gain when they correlate network detection and response (NDR), endpoint detection and response (EDR), and next-generation firewall (NGFW) data across the network. These multi-dimensional analytical and response capabilities help teams detect any evidence of malicious behavior early in the attack life cycle, ultimately accelerating analysis and enabling analysts to respond to issues quickly.
The data provided in this report is the result of the FortiGuard Labs Applied Threat Research (ATR) team’s analysis of more than 11 trillion NDR-originated network events in 2023, which offer insights into the most observed MITRE ATT&CK tactics and techniques attackers used in in that same timeframe to carry out their operations. Any source reporting on “top” ATT&CK techniques is inherently dependent on the lens through which they’re being viewed. This report reveals network-based artifacts that provided FortiNDR Cloud with observations or detections of attacker activity.
MITRE ATT&CK Techniques
Based on our analysis of the detections spotted across the entire MITRE ATT&CK framework, we observed the following trends:
- Widespread use of C2 techniques
- Continued use of commodity remote access trojan (RAT) malware
- Valid accounts are increasingly used for defense evasion
- PowerShell is often used for malicious activity
- Early intrusion discovery techniques are prevalent
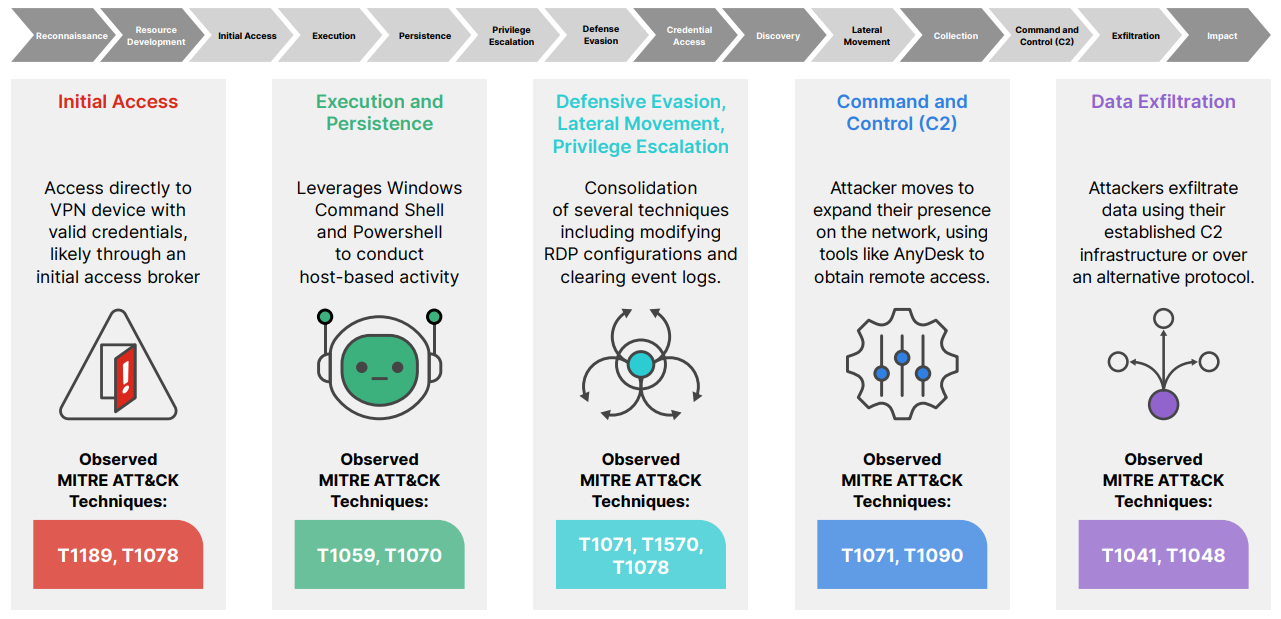
The Rhysida Ransomware Intrusion
When comparing our findings in this report with a real-world attack scenario, such as the Rhysida ransomware intrusion, we can examine specific attacker techniques and share valuable insights into the tactics used by today’s ransomware groups, giving security teams tips for protecting against these malicious activities.
The Rhysida group was first identified in May 2023 when they claimed their first victim. This group deploys a ransomware variant known as Rhysida and offers it as Ransomware-as-a-Service to fellow threat actors via the dark web. Since its arrival, the group has listed at least 50 victims across the world on its website. The group made headlines when it was reported that they had successfully deployed their ransomware in systems associated with the Chilean Army.
Tips for Detecting and Combating Ransomware Attacks
Where the above demonstrates a case study of the techniques employed by Rhysida ransomware operators, there are significant commonalities across various ransomware operators that analysts can use to hunt for and prevent ransomware attacks.
Below are actionable recommendations that security teams can follow to combat ransomware attacks based on these commonalities. The attack techniques outlined here refer to previously observed and mentioned in the report, all mapped to the MITRE ATT&CK framework.