Overview:
Audit your website security with Acunetix Web Vulnerability Scanner
As many as 70% of web sites have vulnerabilities that could lead to the theft of sensitive corporate data such as credit card information and customer lists.
Hackers are concentrating their efforts on web-based applications - shopping carts, forms, login pages, dynamic content, etc. Accessible 24/7 from anywhere in the world, insecure web applications provide easy access to backend corporate databases.
Firewalls, SSL and locked-down servers are futile against web application hacking!
Web application attacks, launched on port 80/443, go straight through the firewall, past operating system and network level security, and right in to the heart of your application and corporate data. Tailor-made web applications are often insufficiently tested, have undiscovered vulnerabilities and are therefore easy prey for hackers.
Find out if your web site is secure before hackers download sensitive data, commit a crime using your web site as a launch pad, and endanger your business. Acunetix Web Vulnerability Scanner crawls your web site, automatically analyzes your web applications and finds perilous SQL injection, Cross site scripting and other vulnerabilities that expose your on line business. Concise reports identify where web applications need to be fixed, thus enabling you to protect your business from impending hacker attacks!
Acunetix - a world-wide leader in web application security
Acunetix has pioneered the web application security scanning technology: Its engineers have focused on web security as early as 1997 and developed an engineering lead in web site analysis and vulnerability detection.
Acunetix Web Vulnerability Scanner includes many innovative features:
- AcuSensor Technology
- An automatic client script analyzer allowing for security testing of Ajax and Web 2.0 applications
- Industries' most advanced and in-depth SQL injection and Cross site scripting testing
- Advanced penetration testing tools, such as the HTTP Editor and the HTTP Fuzzer
- Visual macro recorder makes testing web forms and password protected areas easy
- Support for pages with CAPTHCA, single sign-on and Two Factor authentication mechanisms
- Extensive reporting facilities including VISA PCI compliance reports
- Multi-threaded and lightning fast scanner crawls hundreds of thousands of pages with ease
- Intelligent crawler detects web server type and application language
- Acunetix crawls and analyzes websites including flash content, SOAP and AJAX
- Port scans a web server and runs security checks against network services running on the server
Audit your web site security with Acunetix Web Vulnerability Scanner:
If web applications are not secure, then your entire database of sensitive information is at serious risk. Why?
 |
- Websites and related web applications must be available 24 x 7 to provide the required service to customers, employees, suppliers and other stakeholders;
- Firewalls and SSL provide no protection against web application hacking, simply because access to the website has to be made public
- Web applications often have direct access to backend data such as customer databases and, hence, control valuable data and are much more difficult to secure
- Custom applications are more susceptible to attack because they involve a lesser degree of testing than off-the-shelf software
- Hackers prefer gaining access to the sensitive data because of the immense pay-offs in selling the data.
|
Acunetix Web Vulnerability Scanner (WVS) is an automated web application security testing tool that audits your web applications by checking for exploitable hacking vulnerabilities. Automated scans may be supplemented and cross-checked with the variety of manual tools to allow for comprehensive web site and web application penetration testing.
All Features:
In depth checking for SQL Injection, Cross Site Scripting (XSS) and Other Vulnerabilities with the innovative AcuSensor Technology
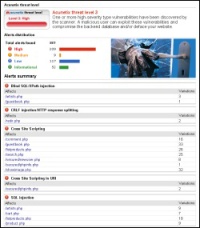
Acunetix checks for all web vulnerabilities including SQL injection, Cross site scripting and others. SQL injection is a hacking technique which modifies SQL commands in order to gain access to data in the database. Cross site scripting attacks allow a hacker to execute a malicious script on your visitor’s browser.
Detection of these vulnerabilities requires a sophisticated detection engine. Paramount to web vulnerability scanning is not the number of attacks that a scanner can detect, but the complexity and thoroughness with the scanner launches SQL injection, Cross Site scripting and other attacks. Acunetix has a state of the art vulnerability detection engine which quickly finds vulnerabilities with a low number of false positives. It also locates CRLF injection, Code execution, Directory Traversal, File inclusion, checks for vulnerabilities in File Upload forms and much more.
Port Scanner and Network Alerts
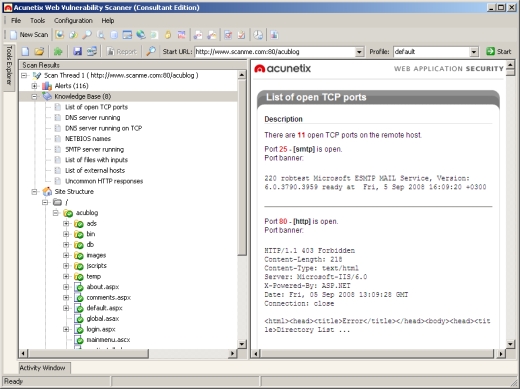
While scanning the website, scan also the web server for open ports and run network alert checks against network services running on the open ports such as DNS cache poisoning and recursion tests, SNMP weak community strings, weak SSH ciphers and many other network services tests. The network alerts checks are scriptable so you can modify them or write new ones yourself.
Advanced penetration testing tools included
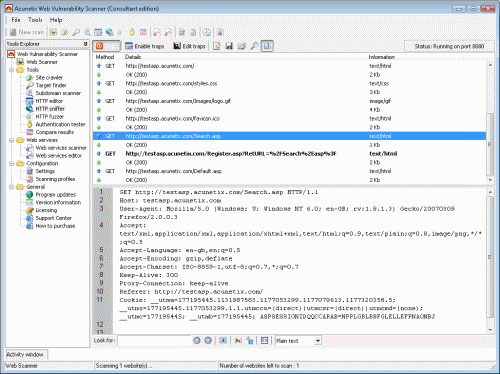
In addition to its automated scanning engine, Acunetix includes advanced tools to allow penetration testers to fine tune web application security checks:
- HTTP Editor - With this tool you can easily construct HTTP/HTTPS requests and analyze the web server response.
- HTTP Sniffer - Intercept, log and modify all HTTP/HTTPS traffic and reveal all data sent by a web application
- HTTP Fuzzer - Performs sophisticated testing for buffer overflows and input validation. Test thousands of input variables with the easy to use rule builder of the HTTP fuzzer. Tests that would have taken days to perform manually can now be done in minutes.
- Blind SQL Injector - Ideal for penetration testers, the Blind SQL injector is an automated database data extraction tool that is perfect for making manual tests that allow further testing for SQL injections.
- Create custom attacks or modify existing ones with the Web Vulnerability Editor
Scan AJAX and Web 2.0 technologies for vulnerabilities
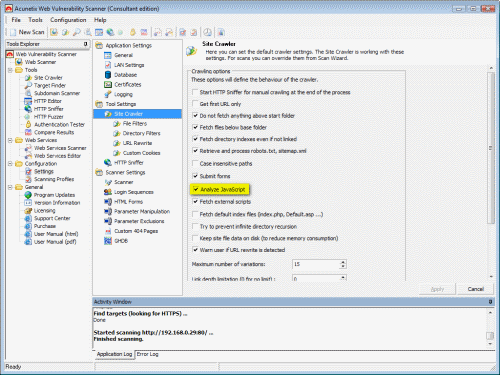
The state of the art CSA (client script analyzer) Engine allows you to comprehensively scan the latest and most complex AJAX / Web 2.0 web applications and find vulnerabilities.
Test password protected areas and web forms with Automatic HTML form filler
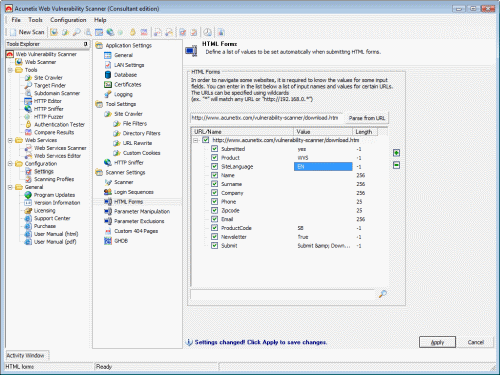
Acunetix Web Vulnerability Scanner is able to automatically fill in web forms and authenticate against web logins. Most web vulnerability scanners are unable to do this or require complex scripting to test these pages. Not so with Acunetix: Using the macro recording tool you can record a logon or form filling process and store the sequence. The scanner can then replay this sequence during the scan process and fill in web forms automatically or logon to password protected areas.
Analyzes your site against the Google Hacking Database
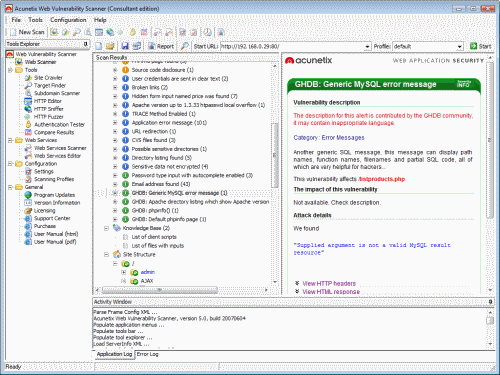
The Google Hacking Database (GHDB) is a database of queries used by hackers to identify sensitive data on your website such as portal logon pages, logs with network security information, and so on. Acunetix launches the Google hacking database queries onto the crawled content of your web site and identifies sensitive data or exploitable targets before a “search engine hacker” does.
AcuSensor Technology – identify more vulnerabilities with less false positives:
Allowing you to identify more vulnerabilities than a traditional black box Web Application Scanner and generating less false positives, Acunetix AcuSensor Technology combines black box scanning techniques with feedback from sensors placed inside the source code while source code is being executed.
The advantages of AcuSensor Technology are many. These include: faster locating and fixing of vulnerabilities, whilst providing more information about each vulnerability, such as source code line number, stack trace and affected SQL query; it also checks for web application configuration problems, such as misconfiguration of web.config or php.ini files; detects many more SQL injection vulnerabilities without depending on web server error messages; and many more.
Finding the right web application scanner; why black box scanning is not enough
Acunetix AcuSensor Technology is a new security technology that allows you to identify more vulnerabilities than a traditional Web Application Scanner, whilst generating less false positives. In addition it indicates exactly where in your code the vulnerability is and reports also debug information.
The increased accuracy is achieved by combining black box scanning techniques with feedback from sensors placed inside the source code while the source code is executed. Black box scanning does not know how the application reacts and source code analyzers do not understand how the application will behave while it is being attacked. Therefore combining these techniques together achieves more relevant results than using source code analyzers and black box scanning independently.
AcuSensor Technology does not require .NET source code; it can be injected in already compiled .NET applications! Thus there is no need to install a compiler or obtain the web applications’ source code, which is a big advantage when using a third party .NET application. In case of PHP web applications, the source is already available.
To date, Acunetix is the leading and only Web Vulnerability Scanner to implement this technology.
Advantages of using Acunetix AcuSensor Technology
- Allows you to locate and fix the vulnerability faster because of the ability to provide more information about the vulnerability, such as source code line number, stack trace, affected SQL query.
- We can significantly reduce false positives when scanning a website because we can internally understand better the behaviour of the web application.
- Can alert you of web application configuration problems which could result in a vulnerable application or expose internal application details. E.g. If ‘custom errors’ are enabled in .NET, this could expose sensitive application details to a malicious user.
- Detect many more SQL injection vulnerabilities. Previously SQL injection vulnerabilities could only be found if database errors were reported or via other common techniques.
- Ability to detect SQL Injection vulnerabilities in all SQL statements, including in SQL INSERT statements. With a black box scanner such SQL injections vulnerabilities cannot be found.
- Ability to know about all the files present and accessible though the web server. If an attacker will gain access to the website and create a backdoor file in the application directory, the file will be found and scanned when using the AcuSensor Technology and you will be alerted.
- AcuSensor Technology is able to intercept all web application inputs and builds a comprehensive list will all possible inputs in the website and tests them.
- No need to write URL rewrite rules when scanning web applications which use search engine friendly URL’s! Using AcuSensor Technology the scanner is able to rewrite SEO URL’s on the fly.
- Ability to test for arbitrary file creating and deletion vulnerabilities. E.g. Through a vulnerable scripta malicious user can create a file in the web application directory and execute it to have privileged access, or delete sensitive web application files.
- Ability to test for email injection. E.g. A malicious user may append additional information such as a list or recipients or additional information to the message body to a vulnerable web form, to spam a large number of recipients anonymously.
How it works
When AcuSensor Technology is used, it communicates with the web server to find out about the web application configuration and the web application platform (such as PHP and .NET) configuration. Once triggered from the Acunetix WVS scanner, the sensor gets a listing of all the files present in the web application directory, even of those which are not linked to through the website. It also gathers a list of all the web application inputs. Since it knows what kind of inputs the application expects, it can launch a broader range of tests against the application.
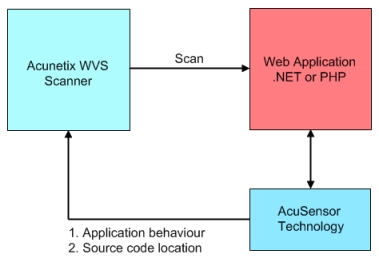
Screenshot 1 - AcuSensor Technology functionality diagram
It has also the ability to scan all SQL transactions taking place between the web application and the database when the web application is being scanned. It hooks between the web application and the database and is able to trace SQL injection vulnerabilities in the code without relying on database errors like other typical scanners do.
AcuSensor Technology vulnerability Reporting
Unlike other vulnerabilities found by typical scans, a vulnerability reported from the AcuSensor Technology contains much more detailed information. As seen in the examples below, it can contain details such as source code line number, stack trace, affected SQL query etc. Each vulnerability found by AcuSensor Technology, will be marked with ‘(AS)’ in the title.
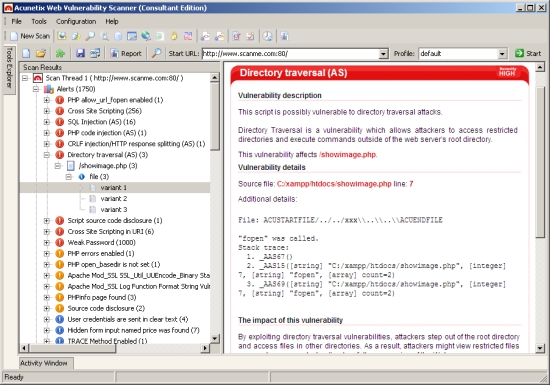
Example 1: SQL Injection reported by Acunetix AcuSensor Technology
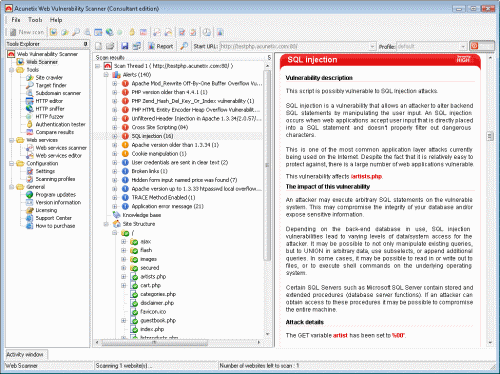
For the reported SQL injection featured in the screenshot below, the SQL query including the injected content which results into an SQL injection vulnerability is shown. The stack trace information is also displayed, to guide the developer where exactly the problem is.
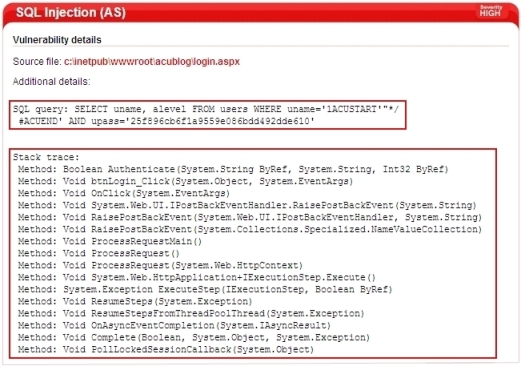
Screenshot 2 - SQL Injection reported by AcuSensor Technology
Example 2: Code Injection reported by Acunetix AcuSensor Technology
For the reported PHP code injection featured in the screenshot below, the vulnerable file name is displayed including the line number of the code which leads to the reported vulnerability. The injected code is also displayed under ‘Attack details’.
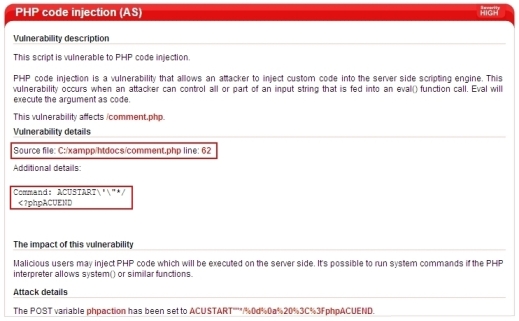
Screenshot 3 - PHP code injection reported by AcuSensor Technology
Conclusion
As seen above, using the AcuSensor Technology has many advantages. Apart from the above mentioned advantages, information provided by the AcuSensor Technology helps the developer trace the vulnerability and fix it in a much shorter time. It also helps them understand what was wrong in the code to allow such vulnerability to happen. From this, developers proactively learn more about vulnerabilities and it helps them in writing more secure code for future web applications and increases web security awareness.
System Requirements:
- Windows XP, Vista, 2000 or Windows 2003 server
- Internet Explorer 6 or higher
- 200 Mb of hard disk space
- 1GB of RAM
Versions Available - Small Business, Enterprise, and Consultant:
Acunetix Web Vulnerability Scanner is available in three versions: A Small Business Version for one nominated web site, an Enterprise version to allow for scanning of an unlimited number of websites, and a Consultant version, which allows you to use Acunetix WVS to perform penetration tests for third parties.
Small Business Version: 1 Nominated Website
The Small Business Version is extended to those organizations owning and operating one website installed on a single server. Ideal for small businesses, this version allows you to scan 1 nominated website and cannot be used to scan sites of customers or third parties.
Enterprise Version: Unlimited Websites
The Enterprise Version is extended to those organizations owning and operating more than one website. Ideal for larger organizations, this allows you to scan an unlimited number of websites and cannot be used to scan sites of customers or third parties.
Consultant Version: Unlimited Websites
The Consultant Version is extended to those organizations scanning any number of websites owned by their customers to provide them with penetration testing and vulnerability assessment services. Ideal for Security Consultants, Web Development Agencies and ISPs, this version also contains the Vulnerability Editor that allows you to create specific types of assessment tests and reports. The Consultant's version also allows you to personalize your reports by adding your own logo.
 Acunetix Web Vulnerability Scanner
Acunetix Web Vulnerability Scanner












