Overview:
Visibility, Zero Trust Access and Incident Response for Connected Assets and Users
FortiNAC™ continues to be a cutting-edge network access control solution, enabling organizations to enforce network access policies and assure adherence to security protocols in light of increasingly sophisticated threats. It provides a comprehensive snapshot of all devices and users on the network, facilitating granular control of access based on user roles, device types, network locations, and now the behavioral patterns of devices and users.
The solution’s capability now extends beyond automated onboarding of new endpoints; it incorporates real-time threat intelligence and continuous risk assessment of devices, leveraging machine learning and AI technologies from FortiGuard Services. Given the rising prominence of BYOD (Bring Your Own Device) and IoT (Internet of Things), FortiNAC’s continuous monitoring and immediate remediation of non-compliant devices have become even more crucial.
Moreover, FortiNAC’s integration goes beyond third-party security solutions; it integrates with a wide range of cloud-based platforms and DevOps tools to ensure seamless and secure network operations in hybrid IT environments. FortiNAC leverages its integration with FortiAnalyzer to gain deep insight into network security posture, encompassing realtime visibility, predictive analytics, and more robust compliance reporting. With FortiNAC, organizations can more effectively secure their network against unauthorized access, potential threats, and increasingly, the insider threats, aligning with the emerging Zero Trust security model that emphasizes “never trust, always verify”
Features
Granular Visibility Across the Network for Every Device and User
FortiNAC leverages AI and machine learning from FortiGuard Security Services to provide detailed profiling of devices, including headless devices and IoT assets on your network. This profiling incorporates multiple information sources, behavior patterns, and real-time threat intelligence to accurately identify and assess what is on your network.
Seamless Integration and Control Across Diverse Environments
With the power of micro-segmentation and Zero Trust policies, FortiNAC allows for configuration changes on switches and wireless products from an extended range of vendors. It amplifies the reach of the Security Fabric across multi-cloud, hybrid IT, and heterogeneous environments, implementing “never trust, always verify’ principles.
Automated Response
FortiNAC reacts to network events in real-time to contain threats before they spread, utilizing a broad and customizable set of automation policies. Leveraging AI, these policies can instantly trigger configuration changes and remediation actions when targeted behavior or anomalies are observed, aligning with the Zero Trust model’s dynamic and proactive approach.
Key Highlights
- Implement dynamic network scanning to classify and analyze device behaviors using continuous, automated techniques
- Maintain an updated inventory of all network devices, including BYOD, IoT, OT, and IoMT
- Continuously assess risks for every endpoint using real-time threat intelligence and behavioral patterns
- Adopt Zero Trust architecture for better device security and simplified management
- Integrate with various third-party network tools ensuring compatibility
- Relay real-time contextual data to SIEM, improving incident response. Ensure always-on identity checks and follow least privilege access, reinforcing the Zero Trust approach
Highlights:
Granular Device Visibility
The essence of securing a dynamic, ever-evolving network lies in comprehending its makeup. FortiNAC leverages AI and machine learning from FortiGuard Security Services, goes beyond merely “seeing” everything on the network—it comprehends and analyzes. It scans your network to discover every user, application, and device. Using a variety of techniques—it profiles each element based on observed behavior, real-time threat intelligence, as well as tapping into FortiGuard’s IoT Services, a cloud-based database for identification lookups
Scanning can be active or passive, utilizing permanent agents, dissolvable agents, or agentless approaches. Moreover, FortiNAC can evaluate a device against pre-approved profiles, noting any discrepancies or software updates required to patch vulnerabilities. With FortiNAC, the network isn’t just known—it’s understood, assessed, and continually monitored.
Besides recognizing the entire network, FortiNAC’s advanced visibility incorporates passive traffic analysis, leveraging Fortinet FortiGate appliances as sensors to identify anomalous behavior patterns. These patterns can indicate a potential compromise, triggering real-time alerts for the SOC team and aligning with the proactive threat containment approach integral to the Zero Trust model.
Network Security and Intelligent Segmentation
After successful classification of devices and user identification, FortiNAC now integrates advanced segmentation techniques to ensure only authorized users and devices have access to requisite resources, thus preventing unauthorized intrusion. Through its progressive rolebased network access control, FortiNAC allows for strategic network segmentation by logically grouping similar data and applications, limiting access to a particular set of users or devices. This strategy effectively confines a compromised device, thereby inhibiting its ability to traverse the network and inflict damage on other resources. FortiNAC not only fortifies the protection of sensitive data and vital assets but also ensures adherence to internal, industrial, and government regulations and mandates
Device Integrity Verification and Malware Prevention
FortiNAC emphasizes on the importance of device integrity prior to network connection, significantly reducing the risk and potential spread of malicious software. As a device attempts to join the network, FortiNAC assesses its configuration for compliance. Any non-compliant configuration is promptly managed; for instance, the device may be allocated to an isolated or restricted access VLAN, devoid of any access to corporate resources. This feature has become increasingly relevant with the rise of IoT devices and remote work trends, ensuring a secure and controlled network environment.
Intelligent Monitoring and Automated Reaction
FortiNAC proactively supervises the network continuously, examining endpoints to verify their compliance with predefined profiles. Leveraging modern security tactics, FortiNAC rescreens devices to prevent any possible bypassing of network access security via MAC-address spoofing. Further, FortiNAC is equipped to identify irregularities in traffic patterns, a vital feature considering the growing complexities in network usage patterns with the rise of cloud and edge computing. This passive anomaly detection function operates symbiotically with FortiGate appliances. Upon recognizing a compromised or susceptible endpoint as a potential risk, FortiNAC promptly instigates an automated reaction, quarantining the endpoint in realtime, furthering its commitment to maintaining a secure and controlled network environment.
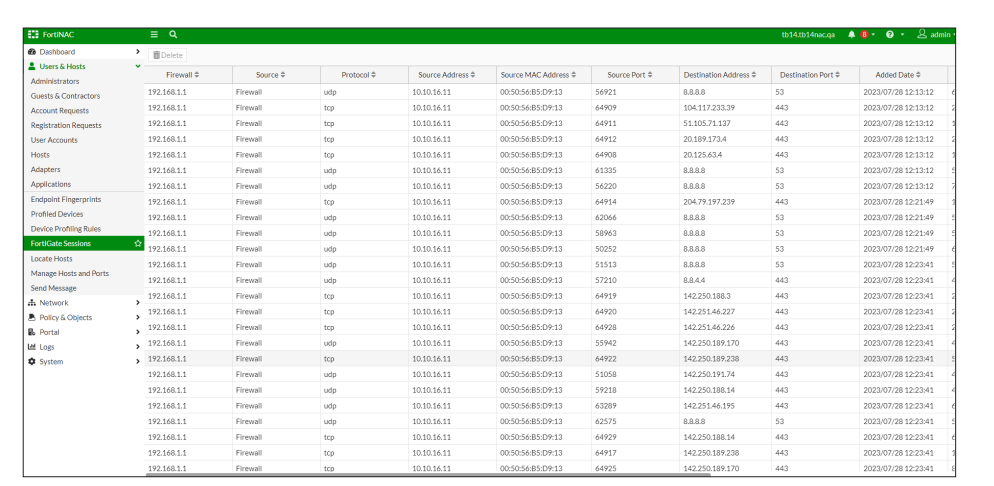
FortiGate Sessions View
The FortiGate Sessions view adds the ability to accept netflow data from third party devices. Flows from other devices would also show up in this view.
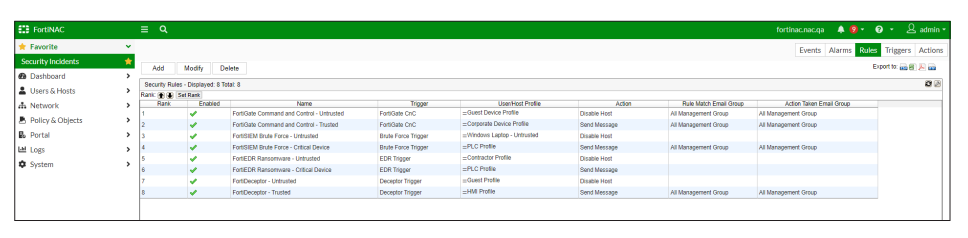
Security Fabric Integrations
FortiNAC integrates with multiple Fortinet products such as FortiGate, FortiSIEM, FortiAnalyzer, FortiEDR, and FortiDeceptor. The Security Rules are triggered by syslog/snmp messages from the other Fortinet products as shown below.
Integration:
Extensive integration with desktop security software, directories, network infrastructure, and third-party security systems provides unparalleled visibility and control across the network environment.
The FortiNAC family integrates
- More than 3000 devices with unique MIB OIDs
- More than 2000 models including switches, access points, and network controllers
- More than 90 vendors in networking, security, and communication industries with the following vendor and models as examples
- Network Infrastructure: Adtran, Aerohive, AlaxalA Networks, Alcatel-Lucent, Allied Telesis, Alteon, APC, Apple, APRESIA Systems, Avaya, Brocade/Foundry Networks/Ruckus, Cisco/Meraki, D-Link, Extreme/Enterasys/Siemens, H3C, HP/Colubris/3Com/Aruba, Intel, Juniper, NEC, Riverbed/Xirrus, and SonicWall
- Security Infrastructure: CheckPoint, Cisco/SourceFire, Cyphort, FireEye, Juniper/ Netscreen, Qualys, Sonicwall, Tenable
- Authentication and Directory Services: RADIUS — Cisco ACS, Free RADIUS, Microsoft IAS, LDAP — Google SSO, Microsoft Active Directory, OpenLDAP
- Operating Systems: Android, Apple MAC OSX and iOS, Linux, Microsoft Windows
- Endpoint Security Applications: Authentium, Avast, AVG, Avira, Blink, Bullguard, CA, ClamAV, Dr. Web, Enigma, ESET, F-Prot, F-Secure, G Data, Intego, Javacool, Lavasoft, Lightspeed, McAfee, Microsoft, MicroWorld, Norman, Norton, Panda, PC Tools, Rising, Softwin, Sophos, Spyware Bot, Sunbelt, Symantec, Trend Micro, Vexira, Webroot SpySweeper, Zone Alarm
- Mobile Device Management: AirWatch, Google GSuite, MaaS360, Microsoft InTune, Mobile Iron, XenMobile, JAMF, Nozomi Networks
Deployment Options
Easy Deployment
FortiNAC is a flexible and scalable solution that spans from mid-size to very large enterprise deployments. There are three elements to the FortiNAC solution.
High Availability
FortiNAC offers High Availability for disaster recovery to ensure redundancy. This state is achieved through active and passive instances where the passive (backup) becomes active when the main is no longer functioning normally. FortiNAC Manager can manage multiple high availability clusters distributed throughout the network as needed.
Centralized Architecture
FortiNAC is an ‘out of band’ solution, meaning it does not sit in-line of user traffic. This architecture allows FortiNAC to be deployed centrally and manage many remote locations. Visibility, control, and response are achieved by integrating with, and leveraging the capabilities of, the network infrastructure. Control can be applied at the point of connection, at the very edge of the network while security device integrations allow FortiNAC to process security alerts and treat them as triggers for automated threat mitigation through customizable work flows.
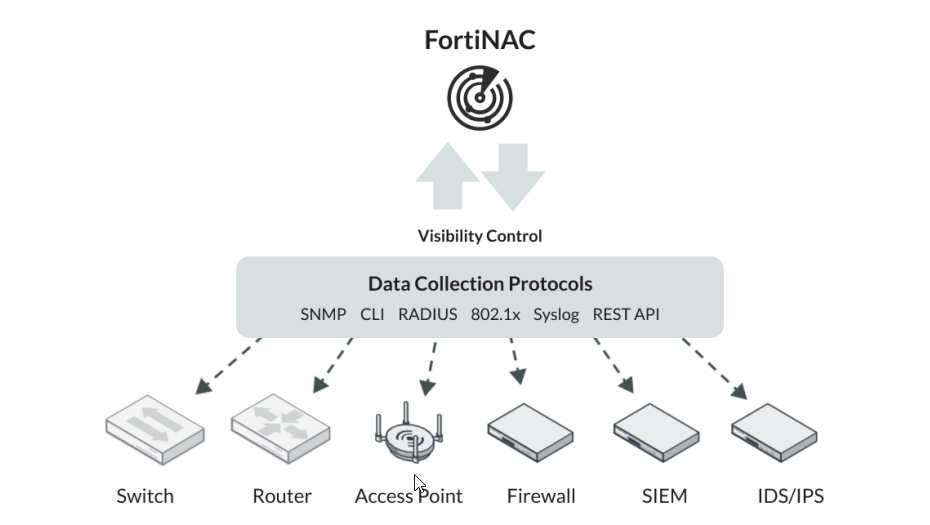
Data collection is gathered from multiple sources using a variety of methods. SNMP, CLI, RADIUS, SYSLOG, API and DHCP fingerprints can all be used to achieve the detailed end-toend visibility necessary to create a truly secure environment.
Licensing:
FortiNAC Licensing
FortiNAC offers flexible deployment options based on the level of coverage and functionality desired.
Base License
The BASE license level provides easy, one-step IoT security solution to close pressing endpoint security gaps by seeing all endpoint devices on the network, automating authorization, and enabling micro-segmentation and network lockdown. The BASE license level is appropriate for organizations that need to secure IoT and headless devices, and enable network lockdown with dynamic VLAN steering, but do not require more advanced user/network controls or automated threat response.
Plus License
The PLUS license level builds on all the functionality of BASE with enhanced visibility and more advanced Network Access Controls and automated provisioning for users, guests, and devices as well as reporting and analytics. The reporting and analytics can greatly assist in providing audit documentation of compliance. The PLUS license level is appropriate for organizations that want complete endpoint visibility and a granular control, but do not require automated threat response.
Pro License
The PRO license level provides the ultimate in visibility, control and response. PRO license offers real-time endpoint visibility, comprehensive access control, and automated threat response and delivers contextual information with triaged alerts. The PRO license level is appropriate for organizations that want complete endpoint visibility, a flexible NAC solution with granular controls, as well as accurate event triage and real-time automated threat response.
Services
FortiCare Services
As your business rapidly evolves, it is critical to advance your security capabilities as well. Often though, you do not have expertise within your organization to deploy, operate, and maintain these new capabilities or are up against tight deadlines to implement change. We understand this challenge and help thousands of organizations every year tackle this problem with FortiCare Services.
Our experts provide accelerated implementation of your technology, reliable assistance through advanced support, and proactive care to ensure your success with Fortinet investment. No matter the size or location of your organization, we are ready to provide you with an elevated experience to help you achieve your business goals with superior security and performance.
FortiCare Support
A FortiCare Support contract entitles you not only to receive updates to the FortiNAC firmware, but also receive two important feeds.
|
FortiNAC LICENSE TYPES |
BASE |
PLUS |
PRO |
| Visibility |
Network |
Network Discovery |
✔ |
✔ |
✔ |
| Rouge Identification |
✔ |
✔ |
✔ |
| Device Profiling & Classification |
✔ |
✔ |
✔ |
| Endpoint |
Enhanced Visiblity |
✔ |
✔ |
✔ |
| Anomaly Detection |
✔ |
✔ |
✔ |
| MDM Integration |
✔ |
✔ |
✔ |
| Persistent Agent |
✔ |
✔ |
✔ |
| User |
Authentication |
|
✔ |
✔ |
| Captive Portal |
|
✔ |
✔ |
| Automation / Control |
Network Access Policies |
✔ |
✔ |
✔ |
| IoT Onboarding with Sponsor |
✔ |
✔ |
✔ |
| Rouge Device Detection & Restriction |
✔ |
✔ |
✔ |
| Firewall Segmentation |
✔ |
✔ |
✔ |
| BYOD / Onboarding |
|
✔ |
✔ |
| Guest Management |
|
✔ |
✔ |
| Endpoint Compliance |
|
✔ |
✔ |
| Web & Firewall Single Sign-on |
✔ |
✔ |
✔ |
| Incident Response |
Event Correlation |
|
|
✔ |
| Extensible Actions & Audit Trail |
|
|
✔ |
| Alert Criticality & Routing |
|
|
✔ |
| Guided Triage Workflows |
|
|
✔ |
| Integrations |
Inbound Security Events |
|
|
✔ |
| Outbound Security Events |
✔ |
✔ |
✔ |
| REST API |
✔ |
✔ |
✔ |
| Reporting |
✔ |
✔ |
✔ |
Specifications:
|
FNC-M-550F |
FNC-CA-600F |
FNC-CA-500F |
FNC-CA-700F |
| CPU |
AMD EPYC 7413 24 Core, 2.65GHz Base Freq |
Intel Xeon E-2278GE 8 Core 3.3GHz Base Freq. |
AMD EPYC 7543P 32 Core, 2.8GHz Base Freq |
| Memory |
32GB DDR4 memory |
16GB DDR4 memory |
96GB DDR4 memory |
| Hard Disk |
2x 960GB SSDs |
2x 960GB SSDs |
2x 960GB SSDs |
| BMC |
N/A |
N/A |
N/A |
| Network Interface |
1x GbE RJ45 and 4x 10GbE SFP+ |
4x GbE RJ45 |
1x GbE RJ45 and 4x 10GbE SFP+ |
| RAID Card |
N/A |
N/A |
N/A |
| RAID Configuration |
Software RAID1 |
Software RAID1 |
| Console Access |
RJ45 type COM port for CLI |
RJ45 type COM port for CLI |
RJ45 type COM port for CLI |
| Form Factor |
1U Rack mountable |
1U Rack mountable |
1U Rack mountable |
| Height x Width x Length (inches) |
1.73 x 17.20 x 24 |
1.73” x 17.32” x 19.69” |
1.73 x 17.20 x 24 |
| Height x Width x Length (mm) |
44 x 437 x 610 |
44 x 437 x 610 |
44 x 437 x 610 |
| Weight |
41 lbs (18.6 kg) |
32 lbs (14.51 kg) |
41 lbs (18.6 kg) |
| Power Supply |
Hot Plug, 1+1 Redundant PSU |
Hot Plug, 1+1 Redundant PSU |
Hot Plug, 1+1 Redundant PSU |
| Input Power |
225 watt |
174 Watt |
375 Watt |
| Input Current |
2.3A@100V, 0.94A@240V |
1.5A@100V; 0.625A@240V |
3.75A@100V, 1.57A@240V |
| Cooling |
5x system fans |
4x system fans |
5x system fans |
| Panel Display |
N/A |
N/A |
N/A |
| Heat Dissipation |
767.731867425 BTU/h |
511.82124495 BTU/h |
1279.553112375 BTU/h |
| Operation Temperature Range |
32°-104°F (0°-40°C) |
32°-104°F (0°-40°C) |
32°-104°F (0°-40°C) |
| Storage Temperature Range |
-4°-158°F (-20°-70°C) |
-4°-158°F (-20°-70°C) |
-4°-158°F (-20°-70°C) |
Humidity (Operating)
Humidity (Non-operating) |
5% to 90% non-condensing |
5% to 90% non-condensing |
5% to 90% non-condensing |
| Safety |
Certified as applicable by Product Safety authorities worldwide, including United States (NRTL), Canada (SCC), and European Union (CE) |
| Electromagnetic (EMC) |
Certified as applicable by EMC authorities worldwide, including United States (FCC), Canada (ICES), European Union (CE). |
| Materials |
Certified as applicable by Materials authorities worldwide, including European Union (ROHS) and China (ROHS). |
Documentation:
Download the Fortinet FortiNAC Datasheet (PDF).







